Overview
In today’s digital world, cyber risk is the top critical concern for businesses of all sizes. Good Cyber risk management involves identifying, assessing, and mitigating cyber risks to protect an organization’s assets, data, and operations.
Cyber risk management involves several key steps, including:
- Identifying potential cyber threats and vulnerabilities
- Assessing the potential impact of these threats
- Implementing measures to mitigate threats
- Implementing an ongoing Cyber Risk Management program

A significant challenge businesses face in managing their cyber risk posture is the constantly evolving threat landscape. Cyber threats continue to become more sophisticated and frequently require businesses to adapt quickly to new threats and vulnerabilities. This is why it is paramount to manage cyber risk through an ongoing program instead of relying on point-in-time cyber risk assessments.
Additionally, businesses struggle to plan financially or connect the potential impacts of cyber attacks and outages to continued business operations, which results in an inability to allocate the necessary resources such as funding, personnel, and time to manage their cyber risk posture. This further makes the case for implementing an ongoing cyber risk management program.
Strategies to successfully assess and manage cyber risk
Organizations need to efficiently understand and actively manage evolving risks so that we can take proactive steps to protect assets, business partners, brands, and continued viability, and ensure competitive advantage in the marketplace.
Having current, up-to-date visibility into organizational exposure to IT and Cyber Risk is critical to an organization’s future success. Consider the following roadmap to security:
- Blueprint for Rapid Visibility: Regulatory Standards and Frameworks provide a structured approach to assessing and managing cyber and regulatory risk.
Examples include:
- NIST CSF
- PCI DSS
- CFR 21 part 11
- CMMC
- FEDRAMP
- GDPR
- GLBA
- HIPAA
- ISO/IEC 27001
- Shared Assessments SIG
- SOC2
- Blueprint for Success:
- Assessment Policy and Process Review
- Infrastructure Review
- Testing
- Gap analysis
- Analysis and Reporting
- Prioritized Risk Registertied to controls,
- Linked to corrective actions, and action items.
- Executive visibility to changes and progress
- Cyber Security Roadmap
- Ongoing Risk Assessment Program: Risk assessment involves identifying potential cyber threats and vulnerabilities and assessing their likelihood and impact. This helps businesses prioritize their cybersecurity efforts and allocate resources effectively
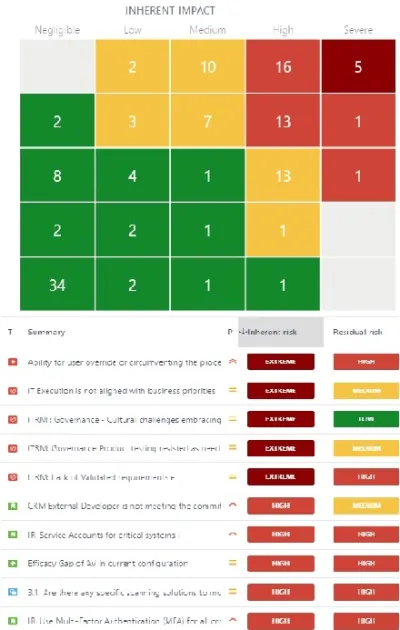
Conclusion
Cyber risk management is a critical concern for businesses in today’s digital world. Businesses must be able to adapt quickly to new threats and vulnerabilities and allocate the necessary resources to effectively manage their cyber risk posture. By leveraging methodologies such as cybersecurity frameworks, risk assessment, penetration testing, and vulnerability scanning, businesses can identify and mitigate cyber risks and proactively protect their assets, data, and operations.
About iLLÜM Advisors
We are passionate about helping our clients overcome IT challenges without simply throwing money away at solutions without a measurement for success. We accomplish this by enabling their existing IT teams to deliver transformative solutions with velocity and improve cyber risk postures.
Our team of senior IT leaders and project managers support our clients with an industry-leading IT management methodology and cyber risk management platform to help organizations of all sizes tackle their most pressing IT challenges. All our service options are provided on a month-to-month basis without long-term commitments.
Click here for more – insights

