Cyber Breach & Incident Response
Cybersecurity breaches are becoming increasingly common in today’s digital world, with businesses facing a wide range of threats including malware, phishing, and social engineering attacks.
“The average cost of a cyber attack for a small business is over $200,000, which can be devastating for businesses with limited resources.” – Small Business Trends.
“According to recent studies, nearly 60% of small businesses that experience a cyber-attack go out of business within six months.” – CNBC
In the event of a cyber breach, it is essential for businesses to have an incident response plan in place to minimize damage and mitigate risk. Today we provide an overview of the types of cyber breaches businesses face and incident response, followed by the challenges and benefits of implementing an incident response plan.
Types of Cyber Breaches
- Malware: Malware is malicious software that is designed to damage or disable computers and systems.
- Phishing: Phishing is a type of social engineering attack that uses fake emails or websites to trick users into revealing sensitive information.
- Ransomware: Ransomware is a type of malware that encrypts and restricts access to a user’s files and demands payment in exchange for the decryption key.
- Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks: DoS and DDoS attacks are designed to overwhelm a network or server with traffic, making it unavailable to customers and users.
Incident Response Overview
Incident response is the process of identifying, containing, and resolving a cyber breach.
“The average time to identify a cyber breach is 206 days, while the average time to contain a breach is 73 days.” – IBM Security
iLLÜM Advisors follows 6 Phases of Incident Response:
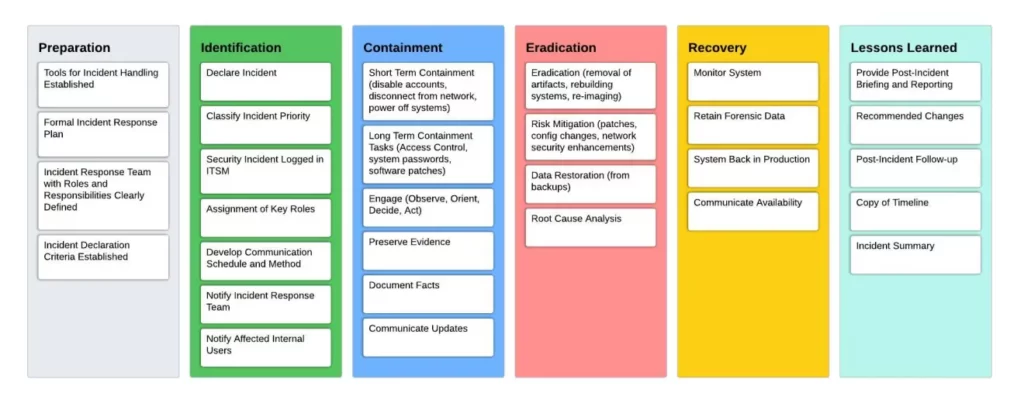
Challenges and Benefits of Implementing an Incident Response Plan
One of the most significant challenges businesses face in implementing an incident response plan is the need for a comprehensive understanding of the organization’s IT infrastructure and potential vulnerabilities. Additionally, businesses may face budget constraints or a lack of resources and expertise to effectively manage an incident response plan.
Benefits of an Incident Response Plan
- Improved Incident Response Time: An incident response plan helps businesses respond quickly and effectively to a cyber breach, minimizing damage and reducing downtime.
- Reduced Financial Losses: An incident response plan can help businesses reduce financial losses by minimizing the impact of a cyber breach.
- Enhanced Reputation: An incident response plan can help businesses preserve their reputation and maintain customer trust by demonstrating a commitment to cybersecurity.
- Compliance: An incident response plan is often required for compliance with regulations such as HIPAA, PCI DSS, and GDPR.
“The average time to detect and contain a cyber breach is significantly shorter for organizations with a mature incident response plan in place.” – CSO Online
Implementing an Incident Response Plan
Implementing an incident response plan may include the following steps –
Define the Scope and Objectives: The first step is to define the scope of the incident response plan and establish clear objectives. This includes identifying the types of incidents that the plan will cover and outlining the roles and responsibilities of the incident response team.
- Develop Incident Response Procedures: Develop detailed procedures for each phase of incident response, including identification, containment, eradication, recovery, and lessons learned. This should include steps to identify the source of the breach, contain the breach, investigate and analyze the breach, and report the breach to the appropriate parties.
- Establish Communication Protocols: Establish communication protocols for all stakeholders, including employees, customers, vendors, and regulatory bodies. This includes defining the chain of command and ensuring that everyone is aware of their roles and responsibilities in the event of a cybersecurity incident.
- Identify Required Resources: Identify the resources required to implement the incident response plan, including technology, personnel, and training. This may include security software, hardware, and IT support personnel, as well as training for the incident response team and other stakeholders.
- Test and Refine the Plan: Regularly test and refine the incident response plan to ensure that it is up-to-date and effective. This includes conducting mock exercises and drills to simulate real-world scenarios and identifying areas for improvement.
- Train Employees and Stakeholders: Ensure that all employees and stakeholders are aware of the incident response plan and understand their roles and responsibilities in the event of a cybersecurity incident. This may include providing training on cybersecurity best practices and ensuring that everyone knows how to report suspicious activity.
Conclusion
Cyber breaches are a significant threat to businesses of all sizes and industries. To effectively manage the risks associated with a cyber breach, businesses need to implement an incident response plan. Although implementing an incident response plan may present some challenges, the benefits, including improved incident response time, reduced financial losses, enhanced reputation, and compliance with regulations, far outweigh the challenges.
About iLLÜM Advisors
At iLLÜM we are passionate about helping our clients overcome IT challenges without simply throwing money at additional technology point solutions. We accomplish this by enabling their existing IT teams to deliver transformative solutions with velocity and improve cyber risk postures.
Our team of senior IT leaders, project managers, and industry-leading IT management platform help organizations of all sizes tackle their most pressing IT challenges. All our service options are provided on a month-to-month for both consultants and software subscriptions, so organizations of all sizes can receive expert IT and cyber security guidance, and project management on-demand, within budget and without the costs associated with long-term commitments.

